DÉPANNAGE À DOMICILE
Sur simple appel ou en remplissant notre formulaire de demande de dépannage, l’un de nos techniciens prend rendez-vous avec vous se déplace à domicile afin de résoudre vos problèmes.
DÉPANNAGE À DISTANCE
PcDuo.fr peut vous aider à distance !
Avec son partenaire TeamViewer, l’un de nos techniciens prend la main sur votre ordinateur, vous dépanne et vous guide, comme s’il était à vos côtés !

LA BOUTIQUE PCDUO.FR
Nous vous accueillons à la boutique si vous avez besoin d’un conseil, d’un consommable (cartouches d’encre, câble, etc.), de faire une photocopie ou de vous connecter à Internet avec l’un de nos ordinateurs.
POUR LES PROFESSIONNELS
Installation et gestion de votre parc informatique, sauvegarde, synchronisation et back-up de vos données, PcDuo.fr propose des services dédiés aux professionnels.
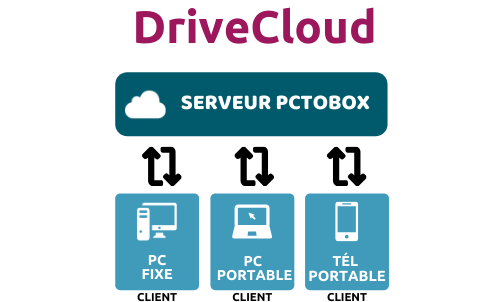
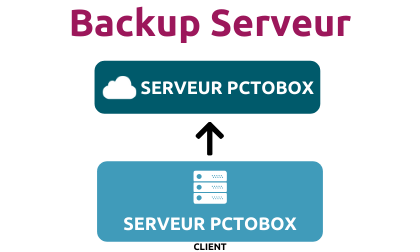
PCTOBOX, LA SÉCURITÉ SANS Y PENSER
PCTOBOX : Solution de sauvegarde de données pour les particuliers et les professionnels
Avec sa solution PCTOBOX, vous n’avez plus besoin de vous préoccuper de vos données, qui sont sauvegardées en toute sécurité.
TARIFS ET ABONNEMENT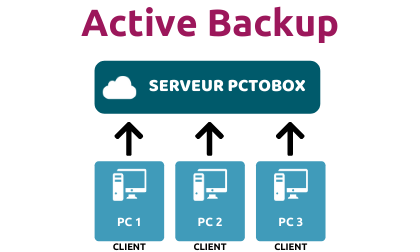
La boutique est à votre service !
La boutique PcDuo est ouverte du Mardi au Samedi de 10h00 à 13h00 et de 14h30 à 19h00.
Vente de matériel
Disques durs, câble HDMI, clés USB, cartouches d’encres ou imprimantes, la boutique PcDuo propose de nombreuses références et si toutefois vous ne trouvez pas votre bonheur, PcDuo vous le commande.
BOUTIQUE EN LIGNEDépannage informatique
Nettoyage, formatage, ou panne matérielle, PcDuo vous répare votre ordinateur.
Accès à internet
La boutique dispose de trois ordinateurs connectés. Vous pouvez travailler librement ou surfer sur Internet.
Photocopies
Pour faire une photocopie, il suffit d’envoyer vos documents à print@pcduo.fr. Vous pouvez également lancer vos impressions depuis un ordinateur de la boutique. Des cartes nominatives sont à votre disposition.
Conseils et aide
Vous avez une question ou vous hésitez sur l’achat d’un matériel, vous pouvez passer à la boutique où grâce à notre expertise, vous y trouverez votre réponse.
Professionnels
Vous souhaitez installer un parc informatique pour vos salariés ou sauvegarder vos données, PcDuo propose ses services aussi à destination des professionnels, start-up ou PME.
EN SAVOIR PLUSDépannage : Comment nous fonctionnons !
PcDuo.fr travaille en toute transparence, de la prise de contact au réglement de la prestation.
1
CONTACTEZ-NOUS
Par téléphone : 01 80 90 50 20
Par e-mail : contact@pcduo.fr
En cliquant sur le bouton ci-dessous
2
ANALYSE
L’un de nos techniciens diagnostique la panne et vous propose un dépannage à domicile ou directement à la boutique.
3
4
RÉGLEMENT DE LA PRESTATION
PcDuo accepte les chèques, les espèces ou les paiements en carte bancaire.
PcDuo.fr peut vous aider à distance avec

PcDuo.fr pour les professionnels
Start-up, petites et moyennes entreprises, PcDuo.fr est le partenaire informatique idéal à Bois-Colombes.
VPN
Connexion au réseau de son entreprise facilement, rapidement et en toute sécurité.
CAMÉRA IP
Installation vidéo surveillance et enregistrement.
TÉLÉPHONIE IP
Mise en place d’abonnements fixe ou virtuels pour votre société.
INTERNET & RÉSEAUX
Packages très hauts débits et personnalisés (fibre dédiée aux professionnels)(avec notre partenaire Keyyo).
PARC INFORMATIQUE
Location et installation d’ordinateurs, configurés selon la taille et les besoins de votre entreprise. Renouvellement de votre parc informatique.
VENTE DE MATÉRIEL INFORMATIQUE
Conseil et vente de matériel informatique au meilleur rapport qualité-prix et correspondant aux besoins de votre entreprise et de vos salariés.
INFOGÉRANCE
Besoin d’aide dans la maintenance de vos outils informatiques ? PcDuo.fr vous propose des contrats d’infogérance sur mesure.
SAUVEGARDE DE DONNÉES
Avec Pctobox, vos données sont sauvegardées et synchronisées automatiquement. Solution 100% sécurisée.
Nos tarifs
Nous proposons un système de facturation transparent, pas de facturation à l’heure, mais au résultat, vous ne payez que le forfait choisi pour l’intervention, pas de surprise lors de la facturation, sur un mode satisfait ou remboursé.
DÉPANNAGES POUR LES PARTICULIERS
- Petite intervention = 10€ TTC
- Prise en charge / Diagnostic = 39€ TTC
- Changement de pièce = 79€ TTC
- Transfert de données (basique) = 69€ TTC
- Installation de logiciel = 69€ TTC
- Réparation système / Nettoyage = 99€ TTC
- Installation mise en réseau = 99€ TTC
- Déplacement = 59€ TTC
- Réinstallation Windows = 99€ TTC
- Récupération de données = 99€ TTC
SERVICES
- Prise de poste = 1€ / 30 minutes
- Connexion Internet = 2€ / heure
- Scan de documents = 1€ / 5 pages
- Photocopie Noir et Blanc = 0.30€
- Photocopie Couleur = 1.20€
YEARS OF EXPERIENCE
L’équipe PcDuo.fr
Afin de répondre à tous vos besoins, l’équipe de PcDuo.fr dispose de tous les savoir-faire nécessaires et est disponible pour vous.
Stéphane
Co-Gérant
Guillaume
Co-Gérant
Raphaël
Technicien

Antoine
Développeur
Comptable
Service comptable
CONTACTEZ-NOUS
Un renseignement ? Une demande de devis, n’hésitez pas à nous contacter avec le formulaire ci-dessous. Nous vous répondrons dans les plus brefs délais.
